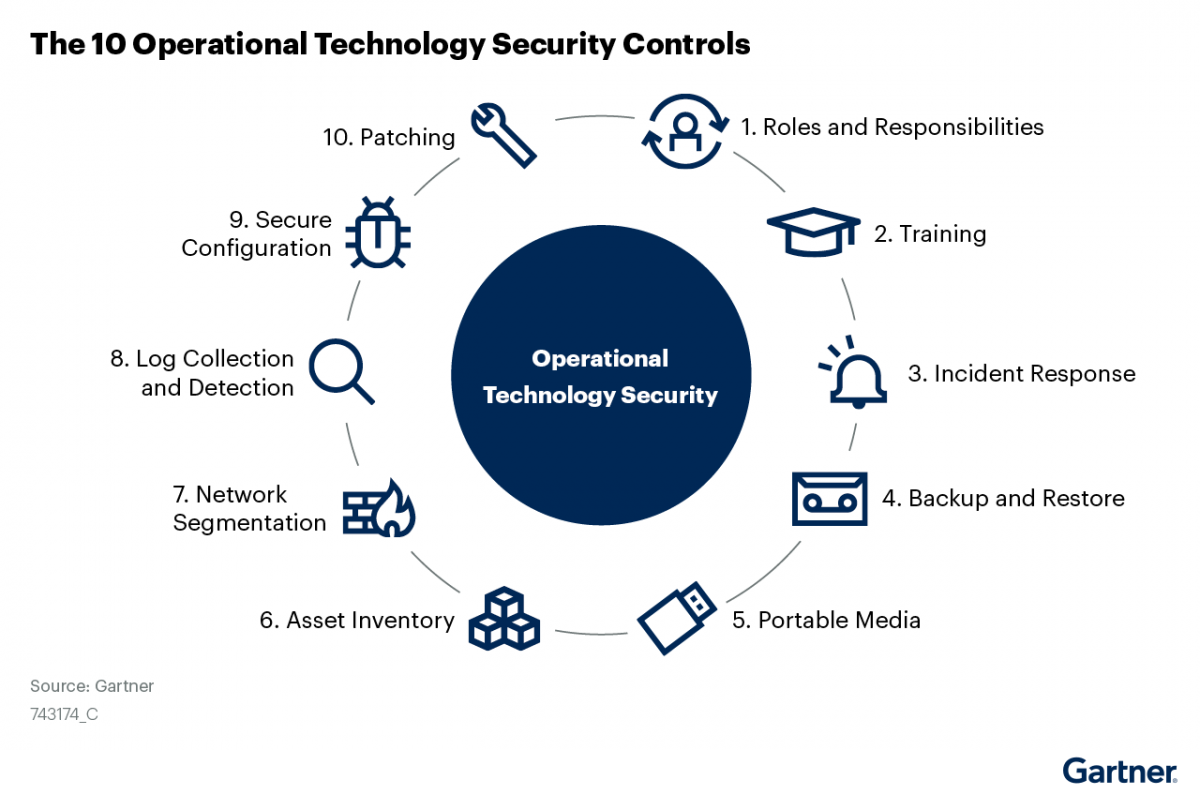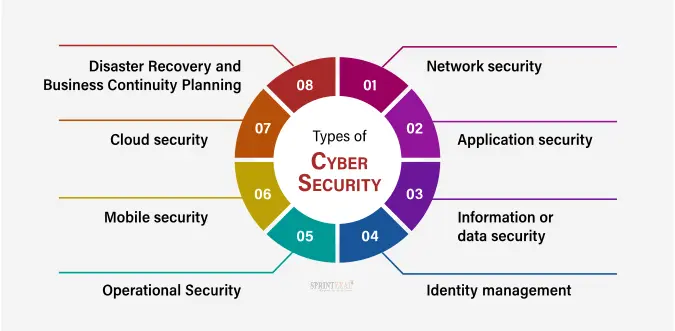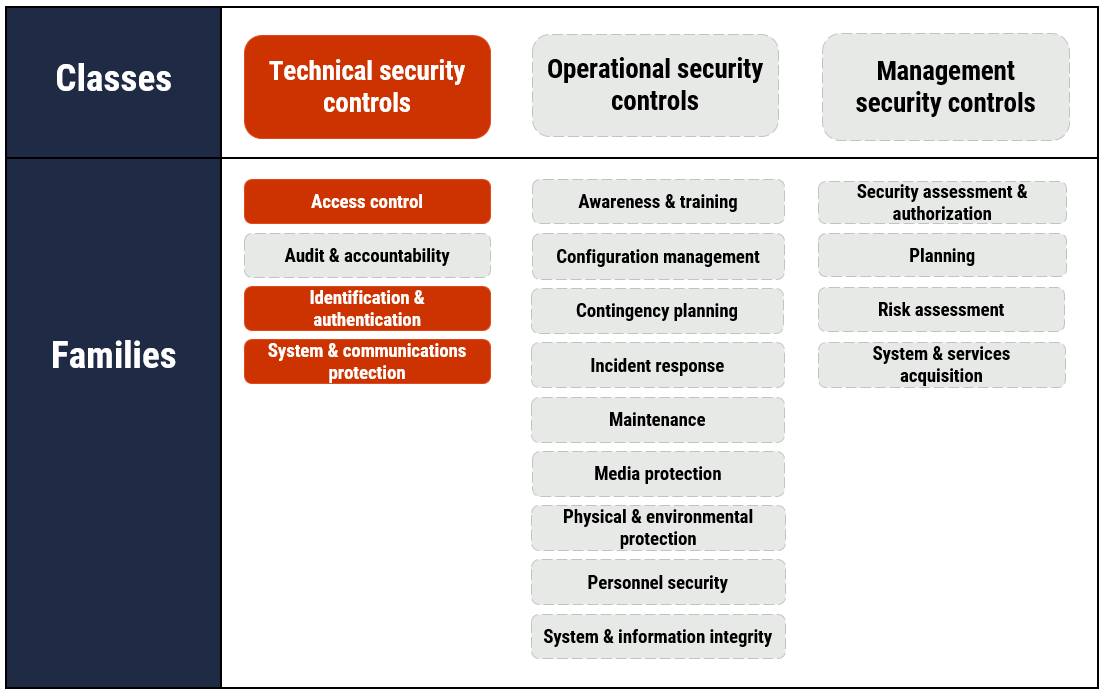
Top 10 IT security actions: No. 3 managing and controlling administrative privileges - ITSM.10.094 - Canadian Centre for Cyber Security

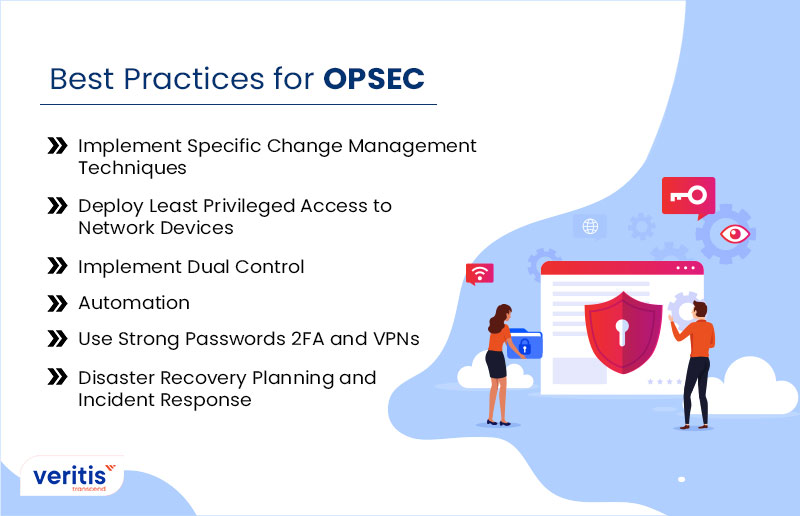
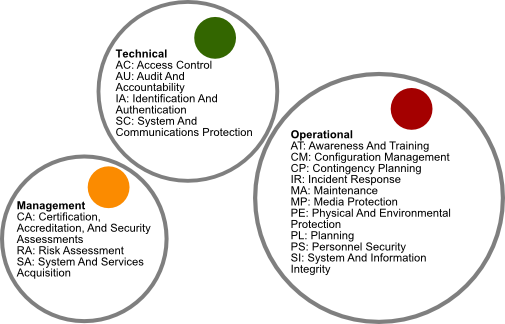
ICS-CERT: Operational Security (OPSEC) for Control Systems – Certificate of Training – Dr. Philip Cao
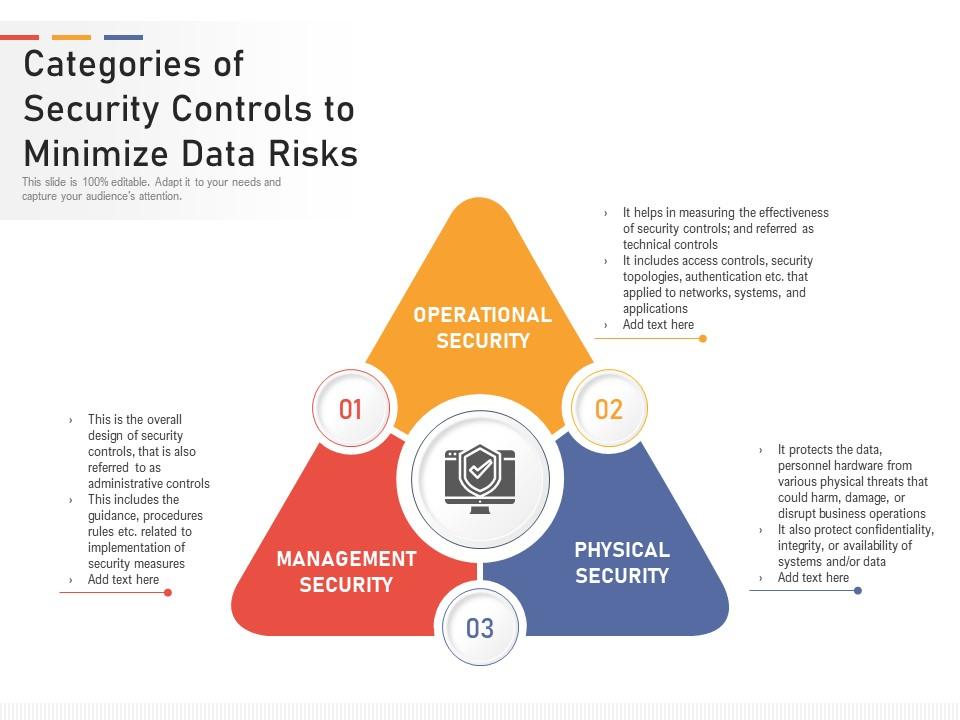
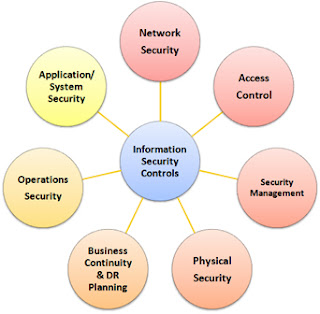
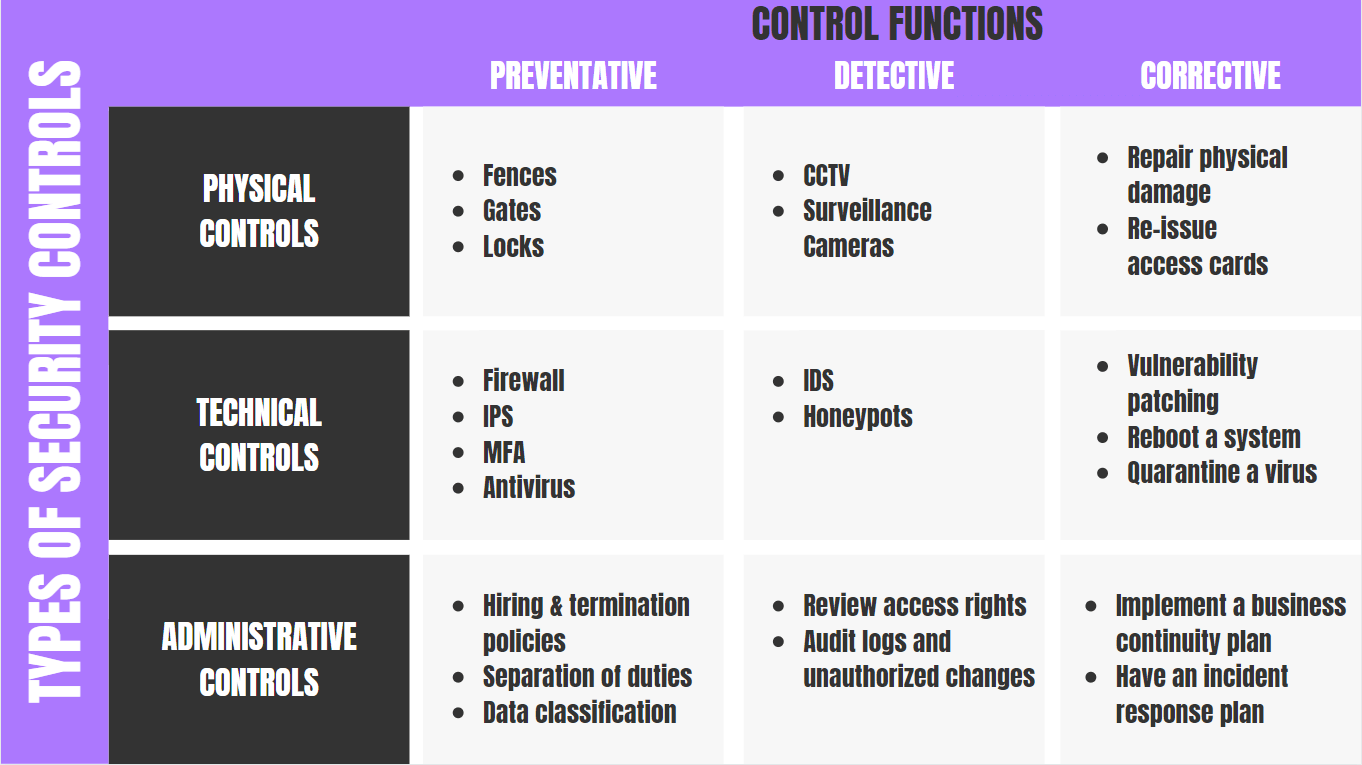
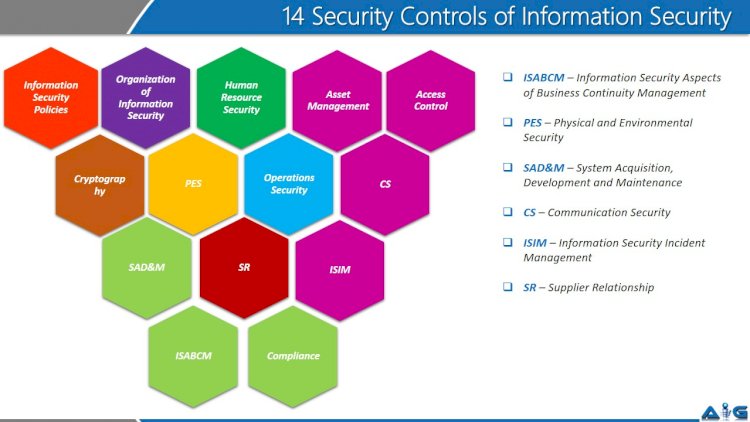
Categories Of Security Controls To Minimize Data Risks | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
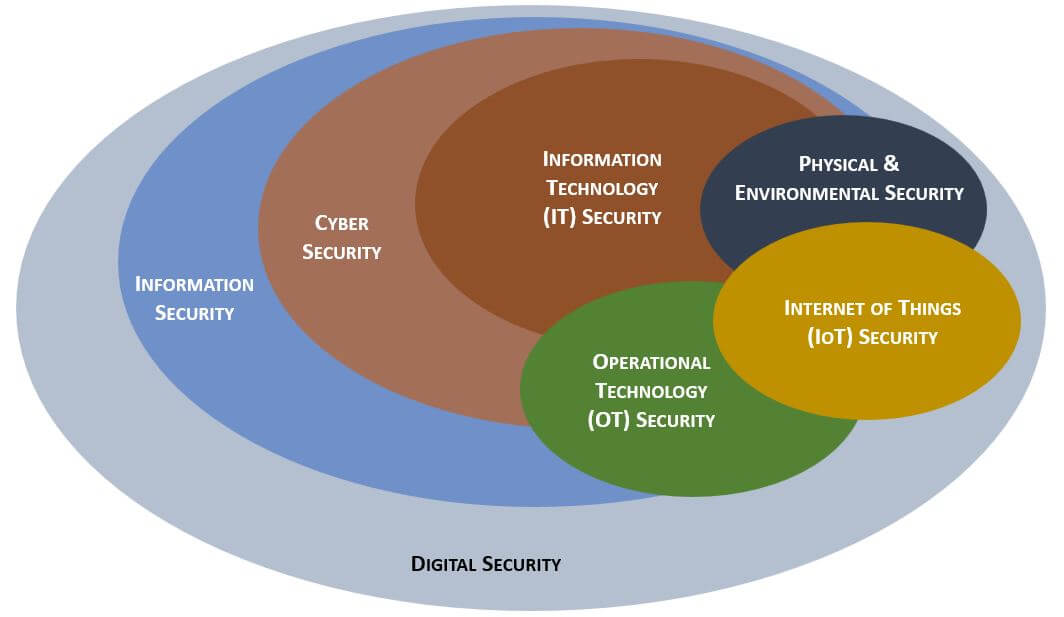
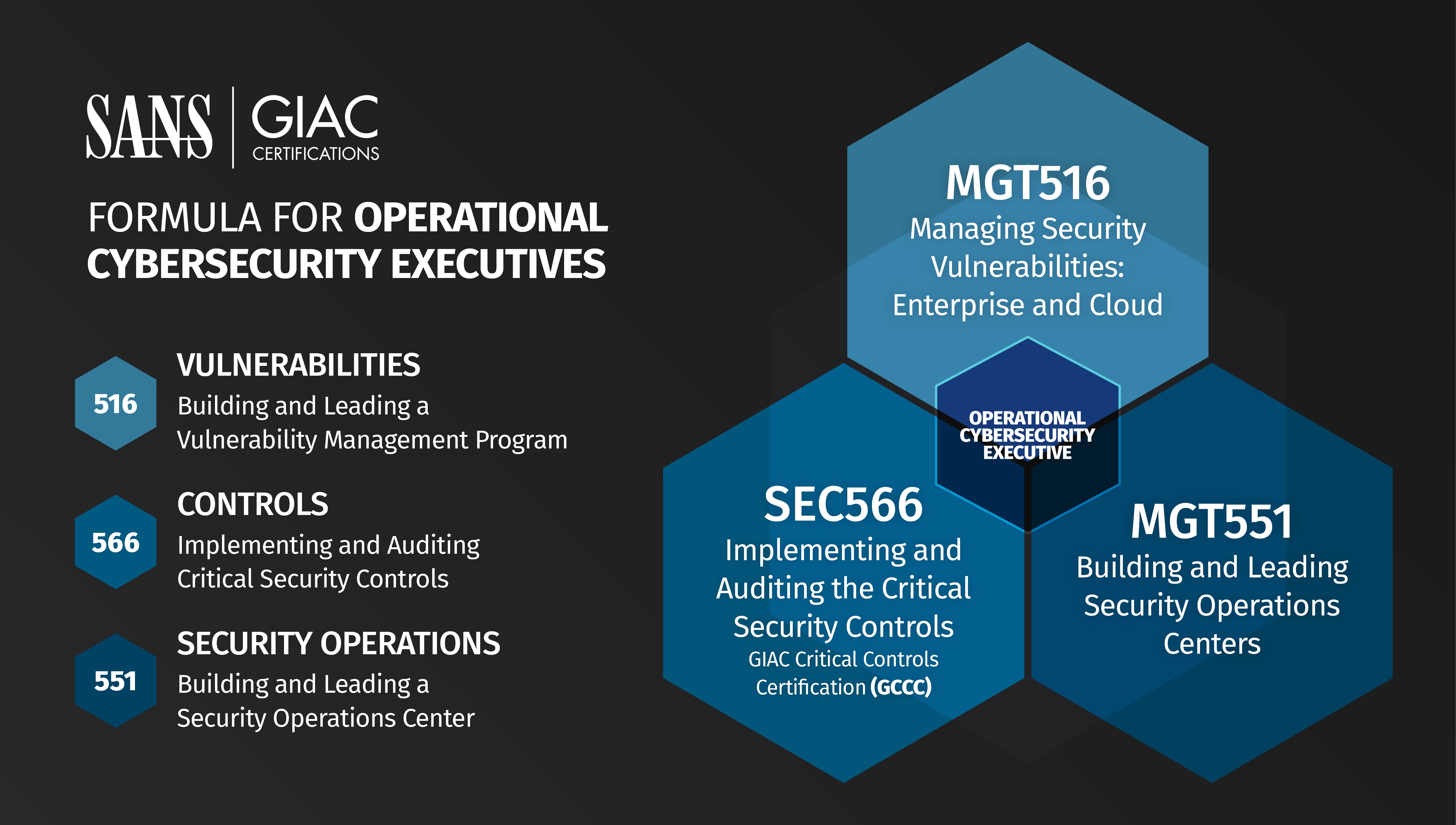
Reasons To Buy - Alignment With Secure Practices - Secure Controls Framework (SCF) - ComplianceForge